By developing from the command line you remain more focused on the task at hand and are less prone to get hung up fighting with your IDE, FTP program or what have you. Upon first making the switch, you'll quickly find that there are many different types of operations that are extremely helpful but require you to authenticate yourself every. single. time. you perform the operation. For example rsync is one of the most useful commands available, but without having your ssh keys set up you can only enjoy half of it's value as you'll have to enter a password every time you run the command. I guess it's worth mentioning that the entire reason for this exercise is so that you don't have to enter your password every time you use ssh either directly or indirectly. Anyway, if you are here you've already found a reason for this so I'll skip right to the good stuff.
Generate Public/Private Keypair
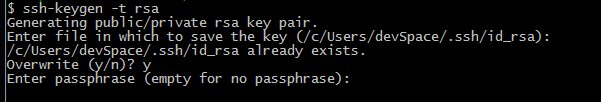
First thing you need to do is create your actual ssh key pair. First navigate to your .ssh directory. The "pair" refers to the two files that are created by running this following command. One key which is a file named id_rsa (no file extension) is for your computer and should live in the ~/.ssh/ directory. The other file named id_rsa.pub is a file we need to move to the server we want to establish our connection with. The command to generate your public/private key pair is quite simple.
ssh-keygen -t rsa |
Follow screen prompts and just press enter when it asks you to enter a password. We are trying to avoid entering our passwords every five seconds after all...
Public Key Goes to Your Server
Once your public/private key pair have been created, copy the id_rsa.pub file to the server you want to set up keys between. Any method you wish to use to copy the file to your server is fine. Filezilla, Bitvise, scp, etc. would all work.
//scp command general syntax
//if using standard port (22) you can omit the p flag
scp -P {portNumber} /path/to/file.ext user@host.com:/home/username/.ssh
//so in our case would look something like this
scp -P 7849 /Users/adminUser/.ssh/id_rsa.pub user1@myhost.com:/home/adminuser/.ssh |
Now you can append that public key to the list of authorized keys. The list of authorized keys is contained within a file called authorized_keys (no file extension). It should live inside of the .ssh directory in the users home directory. If this file doesn't exist, you can just create it and as long as it's named properly and exist in the proper directory your system should recognize it. First, let's create the file if it doesn't exist, and then cat the file to see it's current contents.
//if authorized_keys doesn't exist, just create it like this touch ~/.ssh/authorized_keys //observe both of the file's contents by running the cat command cat ~/.ssh/authorized_keys cat ~/.ssh/id_rsa.pub |
Now let's append the contents of your public key to your authorized_keys file. The two greater than symbols take the output of the command on the left side of the angle brackets and appends it to the file specified on the right side of the angle brackets.
//be sure to use double >> and not a single > //a single bracket will overwrite the entire files contents! cat ~/.ssh/id_rsa.pub >> ~/.ssh/authorized_keys //here's a one liner if you wanna be cool like dat cat ~/.ssh/id_rsa.pub | ssh user@host "mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys" //now observe the file contents //you should see it now contains your development computers public key! cat ~/.ssh/authorized_keys |
Permissions
You need the permissions on ~/.ssh/* to be 400. You also need the permissions on the ~/.ssh/ directory to be 500. This is so other people can't cd into your .ssh directory and steal your keys. Otherwise if it's too open, SSH is like, nah-son, those keys were already stolen, make new ones and lock 'em down! You can accomplish this by running the following commands:
chmod 0500 ~/.ssh/ chmod 0400 ~/.ssh/* |
Viola!! Now you can try connecting to that machine via ssh or any command that runs over the top of ssh and you will no longer be prompted to enter your password. Enjoy!